All About Encryption
By MentorJi in 25 Jun 2024 | 12:33 pmWhat is encryption?, How does encryption work?, What is the purpose of encryption?, Why is encryption important?, What are the different types of encryption?, What is end-to-end encryption?, How does end-to-end encryption work?, What is the difference between encryption and decryption?, What is an encryption key?, How secure is encryption?, What are some common encryption algorithms?, How is encryption used in online transactions?, What is the difference between symmetric and asymmetric encryption?, How does public key encryption work?, What are the benefits of end-to-end encryption?, Can encrypted data be hacked?, What are some challenges associated with encryption?, How does encryption protect data in transit?, What is the role of encryption in cybersecurity?, How do businesses use encryption to protect customer data?, What are the risks of not using encryption?, How does encryption work in messaging apps?, Can service providers read messages with end-to-end encryption?, What is encryption in transit?, What is the difference between end-to-end encryption and encryption in transit?, How can you tell if a website is using encryption?, What is the role of SSL/TLS in encryption?, How does encryption affect data privacy?, What are the legal implications of using encryption?, Why do some governments oppose end-to-end encryption?, How can you implement encryption in your systems?, What are some best practices for using encryption?, How does encryption protect against hackers?, Are there any downsides to encryption?, How does quantum computing impact encryption?, What is homomorphic encryption?, How does encryption impact performance?, How is encryption used in email security?, What are the latest trends in encryption technology?, How do encryption and hashing differ?, What is the future of encryption?
 What is encryption?
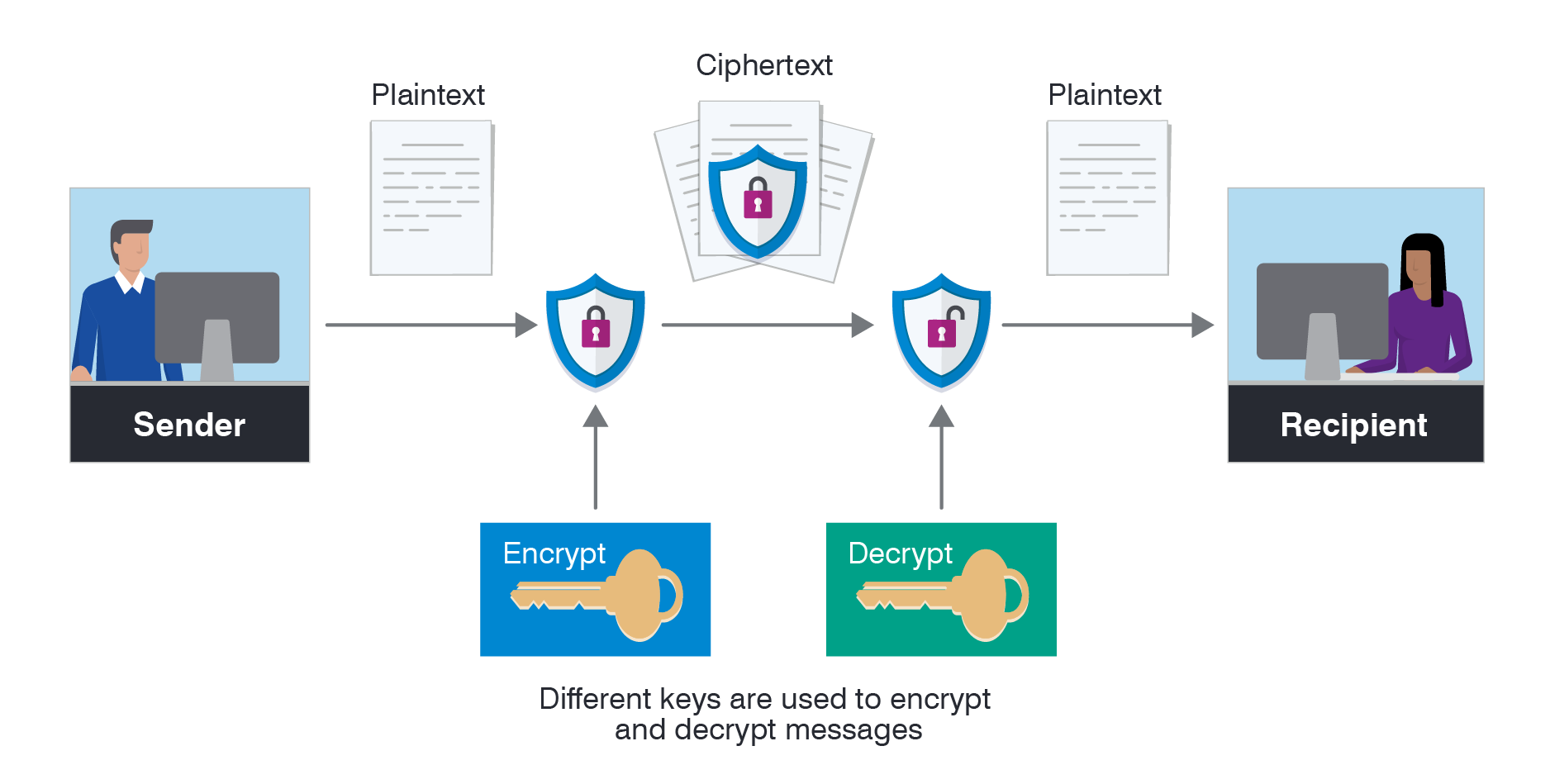
What is encryption?
Encryption is a process that converts information or data into a code to prevent unauthorized access.
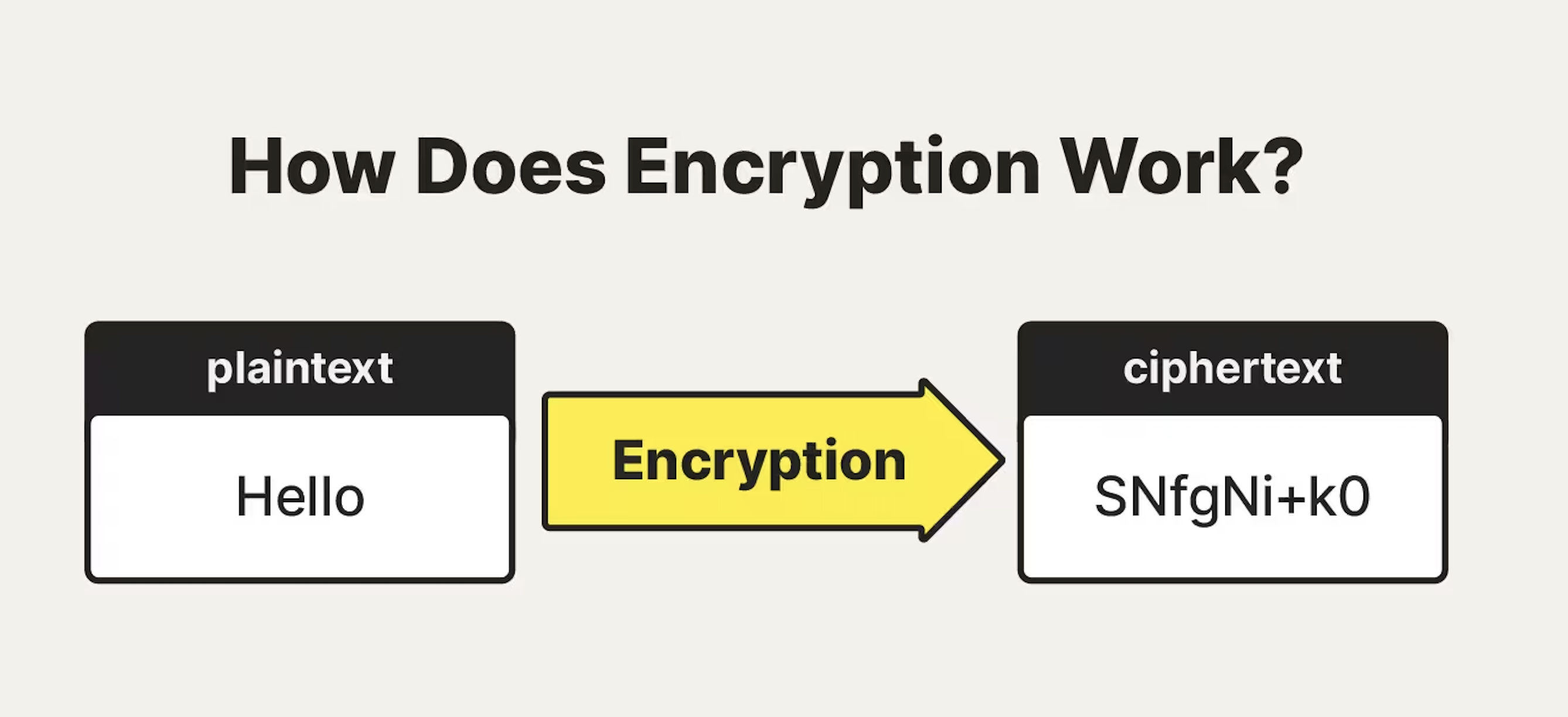
How does encryption work?
Encryption works by using an algorithm to convert the original data (plaintext) into a coded version (ciphertext) using a key. Only those with the appropriate key can decrypt the ciphertext back into plaintext.
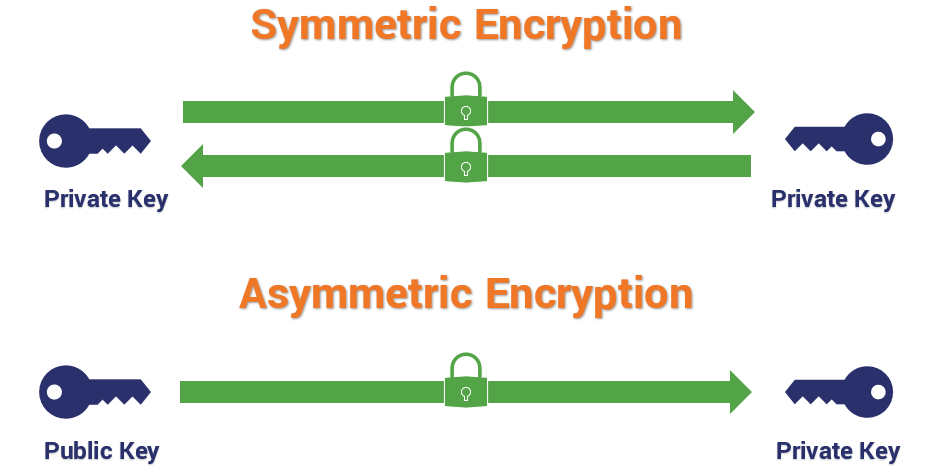
What are the different types of encryption?
The different types of encryption include symmetric encryption, asymmetric encryption, and hashing.
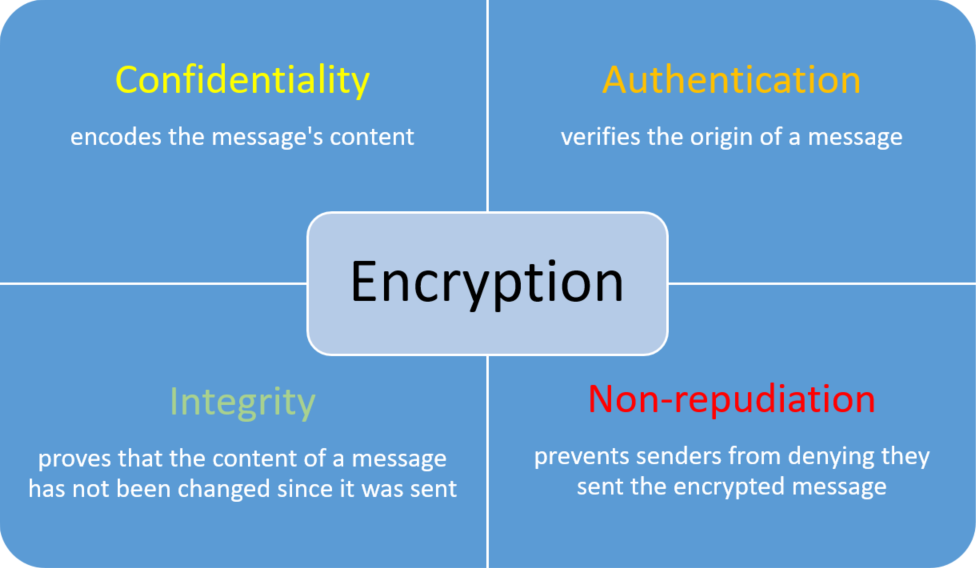
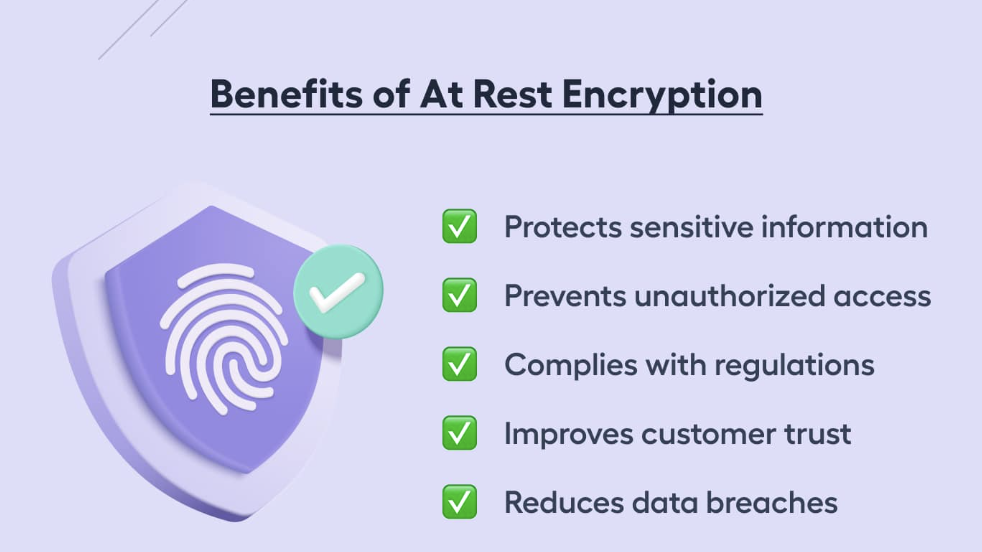
What is the purpose of encryption?
The purpose of encryption is to protect sensitive information from unauthorized access, ensuring privacy and data security.
Why is encryption important?
Encryption is important because it secures data from hackers, ensures privacy, and maintains the integrity of information during transmission.
What is end-to-end encryption?
End-to-end encryption (E2EE) ensures that data is encrypted on the sender’s device and only decrypted on the recipient’s device, preventing anyone else from accessing the data during transmission.
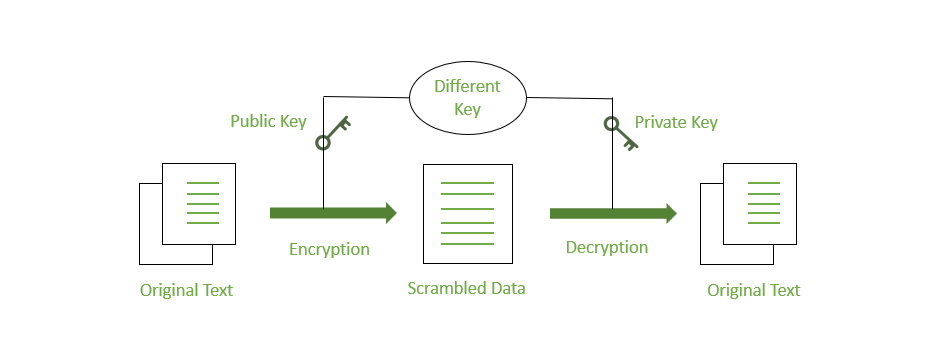
How does end-to-end encryption work?
End-to-end encryption works by using a pair of keys (public and private). The sender encrypts the data with the recipient's public key, and the recipient decrypts it with their private key.
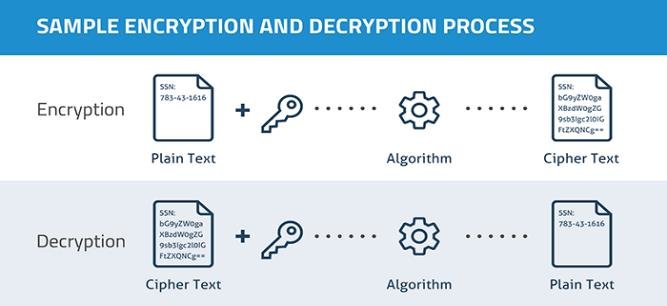
What is the difference between encryption and decryption?
Encryption converts plaintext into ciphertext, while decryption converts ciphertext back into plaintext using the appropriate key.
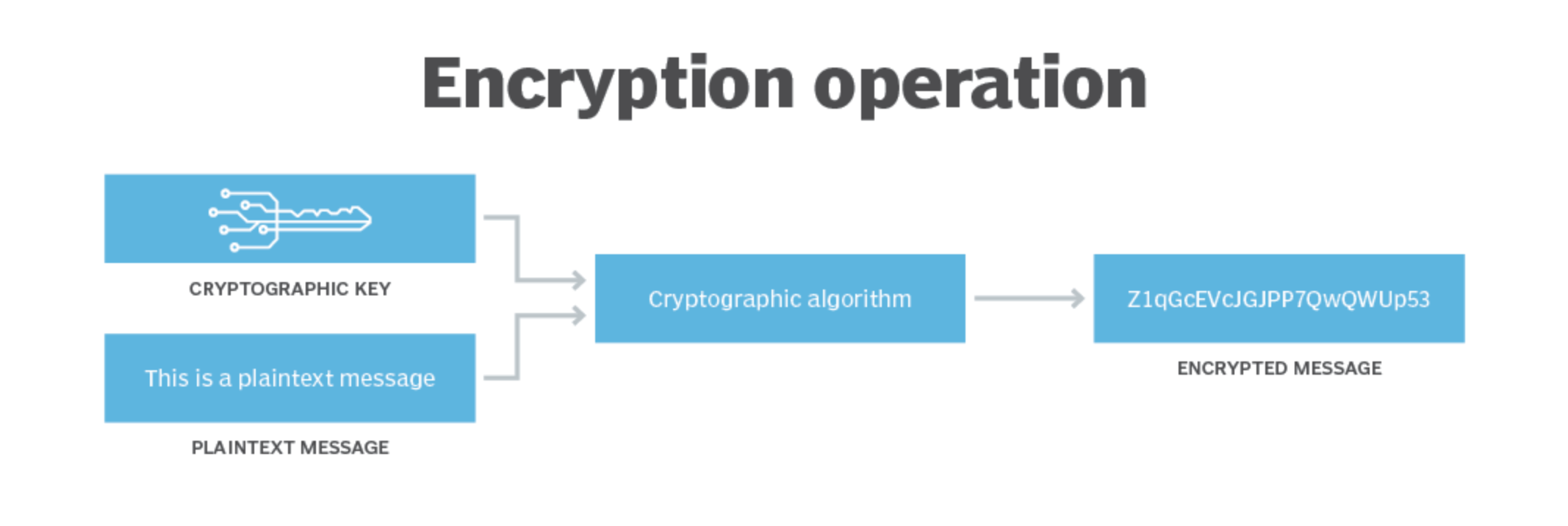
What is an encryption key?
An encryption key is a piece of information that determines the output of the encryption algorithm, allowing data to be encrypted and decrypted.
How secure is encryption?
Encryption is highly secure when strong algorithms and sufficiently long keys are used, but it can be vulnerable to brute force attacks, key theft, or implementation flaws.
What are some common encryption algorithms?
Common encryption algorithms include AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), and DES (Data Encryption Standard).
How is encryption used in online transactions?
Encryption in online transactions secures data such as credit card numbers and personal information by encoding it during transmission to prevent interception by unauthorized parties.
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses a pair of keys—a public key for encryption and a private key for decryption.
How does public key encryption work?
Public key encryption involves two keys: a public key that can be shared with anyone to encrypt data, and a private key that is kept secret to decrypt the data.
What are the benefits of end-to-end encryption?
End-to-end encryption ensures data privacy, protects against eavesdropping, and ensures that only the intended recipient can read the message.
Can encrypted data be hacked?
Encrypted data can be hacked if weak encryption algorithms are used, if the keys are compromised, or through brute force attacks, although strong encryption is generally very secure.
What are some challenges associated with encryption?
Challenges include managing and storing encryption keys, ensuring compatibility across different systems, and maintaining performance while using encryption.

